Dos 攻撃 - DDoS攻撃とは!事例と3つの対策を解説【担当者向け資料一覧付】
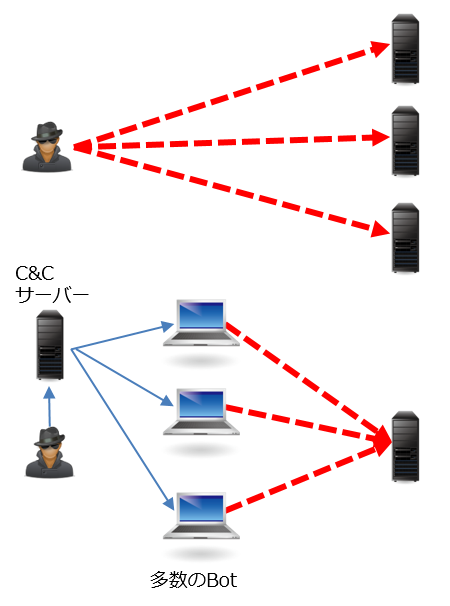
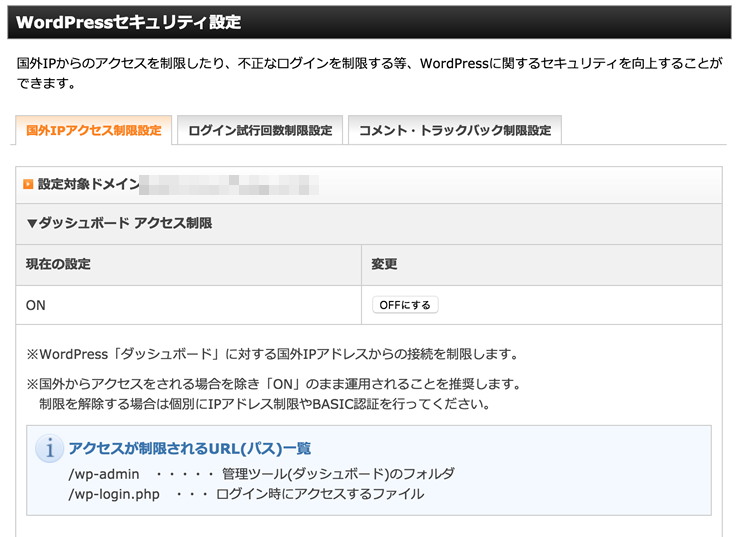
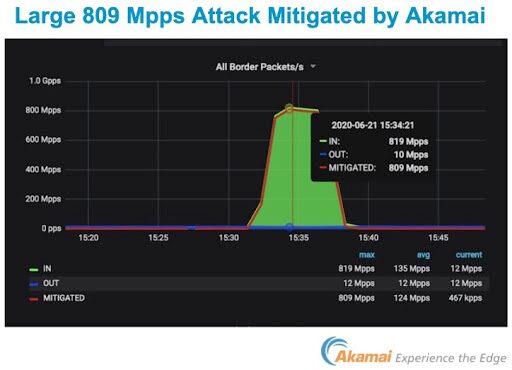
IEEE Transactions on Computers. Because the source IP addresses can be trivially spoofed, an attack could come from a limited set of sources, or may even originate from a single host. Its DoS mechanism was triggered on a specific date and time. Unlike MyDoom's DDoS mechanism, botnets can be turned against any IP address. UK's has tools built for DDoS, named PREDATORS FACE and ROLLING THUNDER. The network company has described this attack as the "Stupidly Simple DDoS Protocol". Attacks may use specific packet types or connection requests to saturate finite resources by, for example, occupying the maximum number of open connections or filling the victim's disk space with logs. Unlike the distributed denial-of-service attack, a PDoS attack exploits security flaws which allow remote administration on the management interfaces of the victim's hardware, such as routers, printers, or other. With a of thousands of devices, the attackers can generate sufficient packet rates and occupy bandwidth to saturate links, causing the denial of services. Social media users, while waiting for the Wikipedia recovery, created a "", WikipediaDown, on in an effort to draw public attention. When the victim scales back down, the attack resumes, causing resources to scale back up again. This reflected attack form is sometimes called a "DRDOS". It has been reported that there are new attacks from IoT devices that have been involved in denial of service attacks. These collections of compromised systems are known as. When the consumer objects, the scammer retaliates by flooding the victim's employer with thousands of automated calls. Bandwidth-saturating floods rely on the attacker's ability to generate the overwhelming flux of packets. Security experts recommend targeted websites to not pay the ransom. It uses a layered structure where the attacker uses a to connect to handlers, which are compromised systems that issue commands to the zombie agents, which in turn facilitate the DDoS attack. Europol said UK police were conducting a number of "live operations" targeting over 250 users of Webstresser and other DDoS services. Malware can carry DDoS attack mechanisms; one of the better-known examples of this was. An analogy is to a bricks-and-mortar department store where customers spend, on average, a known percentage of their time on different activities such as picking up items and examining them, putting them back, filling a basket, waiting to pay, paying, and leaving. But if it did this routinely, were a mob to start showing up but never buying anything, this could ruin the store with the extra employee costs. It is very simple to launch, the primary requirement being access to greater than the victim. It also makes it difficult to distinguish legitimate user traffic from attack traffic when spread across multiple points of origin. Some common examples of DDoS attacks are , and. The company appears to have taken advantage of the situation, with utube. Agents are compromised via the handlers by the attacker using automated routines to exploit vulnerabilities in programs that accept remote connections running on the targeted remote hosts. This might be a university website setting the grades to be available where it will result in many more login requests at that time than any other. An based IPS may detect and block denial-of-service attacks because they have the and the granularity to analyze the attacks and act like a in an automated way. In October 2016, a Mirai botnet attacked Dyn which is the ISP for sites such as Twitter, Netflix, etc. PhlashDance is a tool created by Rich Smith an employee of Hewlett-Packard's Systems Security Lab used to detect and demonstrate PDoS vulnerabilities at the 2008 EUSecWest Applied Security Conference in London. This becomes amplified when using botnets that all send requests with the same spoofed IP source, which will result in a massive amount of data being sent back to the victim. Another early demonstration of DoS attack was made by Khan C. In essence, these technique are statistical methods of assessing the behavior of incoming requests to detect if something unusual or abnormal is going on. In 2013, application-layer DDoS attacks represented 20% of all DDoS attacks. SNMP and can also be exploited as reflector in an amplification attack. A common way of achieving this today is via distributed denial-of-service, employing a. The previous record had been set a few days earlier, on March 1, 2018, when GitHub was hit by an attack of 1. DDoS Attacks in Service Clouds. These response packets are known as backscatter. Since the size of the request is significantly smaller than the response, the attacker is easily able to increase the amount of traffic directed at the target. In the , were used to flood political opponents with spurious calls to jam phone banks on election day. While this may make it more difficult for legitimate customers to get served during the mob's presence, it saves the store from total ruin. More sophisticated attackers use DDoS tools for the purposes of — including against their business rivals. Once the hacker has acquired the desired number of bots, they instruct the bots to try to contact an ISP. Also, many security tools still do not support IPv6 or may not be configured properly, so the firewalls often might get bypassed during the attacks. The process typically involves an attacker sending a DNS name look up request to a public DNS server, spoofing the source IP address of the targeted victim. The founders of Telegram have stated that this attack appears to be that of a "State sized actor" via IP addresses originating in China. US-CERT have observed that different services may result in different amplification factors, as tabulated below: UDP-based Amplification Attacks Protocol Bandwidth Amplification Factor 50000 fixed in version 1. Although in September 2009, a vulnerability in was referred to as a "teardrop attack", this targeted which is a higher layer than the TCP packets that teardrop used. In this scenario, attackers with continuous access to several very powerful network resources are capable of sustaining a prolonged campaign generating enormous levels of un-amplified DDoS traffic. Many sites' servers thought the requests were from a virus or spyware trying to cause a denial-of-service attack, warning users that their queries looked like "automated requests from a or spyware application". Marketed and promoted as stress-testing tools, they can be used to perform unauthorized denial-of-service attacks, and allow technically unsophisticated attackers access to sophisticated attack tools. This scenario primarily concerns systems acting as servers on the web. Main article: Attackers have found a way to exploit a number of bugs in servers to initiate DDoS attacks. It is notable that unlike many other DDoS or DDoS attacks, which try to subdue the server by overloading its network or CPU, an HTTP slow POST attack targets the logical resources of the victim, which means the victim would still have enough network bandwidth and processing power to operate. Each handler can control up to a thousand agents. The attacker generates a flood of traffic until a cloud-hosted service scales outwards to handle the increase of traffic, then halts the attack, leaving the victim with over-provisioned resources. Most devices on a network will, by default, respond to this by sending a reply to the source IP address. Much like , RUDY keeps sessions at halt using never-ending POST transmissions and sending an arbitrarily large content-length header value. For example, SYN flood can be prevented using delayed binding or TCP splicing. The response overwhelmed the company's servers. Similar unintentional denials-of-service can also occur via other media, e. HTTP slow POST attacks are difficult to differentiate from legitimate connections and are therefore able to bypass some protection systems. In some cases, displayed caller ID is spoofed to impersonate police or law enforcement agencies. In general, the victim machine cannot distinguish between the spoofed packets and legitimate packets, so the victim responds to the spoofed packets as it normally would. It uses short synchronized bursts of traffic to disrupt TCP connections on the same link, by exploiting a weakness in TCP's re-transmission timeout mechanism. This type of DDoS involved hardcoding the target IP address prior to releasing the malware and no further interaction was necessary to launch the attack. It is very difficult to defend against these types of attacks because the response data is coming from legitimate servers. This is typically done through publicly accessible servers that are used to cause congestion on the target system using DNS response traffic. Archived from PDF on 2011-02-26. In the OSI model, the definition of its is narrower in scope than is often implemented. In fact, any attack against availability would be classed as a denial-of-service attack. Agents are compromised via the handlers by the attacker. July 2017 , the third-oldest ISP in the world, was the target of what is thought to be the first DoS attack. If the sum of the offset and size of one fragmented packet differs from that of the next fragmented packet, the packets overlap. In November 2017; Junade Ali, a Computer Scientist at noted that whilst network-level attacks continue to be of high capacity, they are occurring less frequently. The term "backscatter analysis" refers to observing backscatter packets arriving at a statistically significant portion of the space to determine characteristics of DoS attacks and victims. On March 5, 2018, an unnamed customer of the US-based service provider fell victim to the largest DDoS to that date, reaching a peak of about 1. March 2018 Approaches to DDoS attacks against cloud-based applications may be based on an application layer analysis, indicating whether incoming bulk traffic is legitimate and thus triggering elasticity decisions without the economical implications of a DDoS attack. These attacks can use different types of internet packets such as: TCP, UDP, ICMP etc. The worm propagates through networks and systems taking control of poorly protected IoT devices such as thermostats, Wi-Fi enabled clocks and washing machines. Criminal perpetrators of DoS attacks often target sites or services hosted on high-profile such as banks or. Essentially, a sophisticated DDoS attack is lower in cost due to its use of less traffic, is smaller in size making it more difficult to identify, and it has the ability to hurt systems which are protected by flow control mechanisms. According to the researchers, the most effective way to stop this attack is for companies to lock down UPnP routers. HUAWEI CLOUD-Grow With Intelligence. Jonathan Looney discovered -, CVE-, CVE- on June 17, 2019. The attacker will send large numbers of packets with the source address faked to appear to be the address of the victim. It can be used on networks in conjunction with routers and switches. A DoS or DDoS attack is analogous to a group of people crowding the entry door of a shop, making it hard for legitimate customers to enter, thus disrupting trade. This could be caused when a server provides some service at a specific time. Proceedings of the 11th International Conference on Cloud Computing and Services Science. This type of attack, referred to as degradation-of-service, can be more difficult to detect and can disrupt and hamper connection to websites for prolonged periods of time, potentially causing more overall disruption than a denial-of-service attack. This can happen when an extremely popular website posts a prominent link to a second, less well-prepared site, for example, as part of a news story. In 2006, sued : massive numbers of would-be YouTube. These attack requests are also sent through UDP, which does not require a connection to the server. Disruption lasted anywhere from hours to days. Denial of service is typically accomplished by flooding the targeted machine or resource with superfluous requests in an attempt to overload systems and prevent some or all legitimate requests from being fulfilled. A small request to this time server can be sent using a spoofed source IP address of some victim, which results in a response 556. The banker's attempt to contact the victim for verification of the transfer fails as the victim's telephone lines are being flooded with thousands of bogus calls, rendering the victim unreachable. Exposure of degradation-of-service attacks is complicated further by the matter of discerning whether the server is really being attacked or is experiencing higher than normal legitimate traffic loads. Statements consisting only of original research should be removed. Archived from on 19 June 2019. A string of out-of-band data was sent to port 139 of the victim's machine, causing it to lock up and display a. In some cases a machine may become part of a DDoS attack with the owner's consent, for example, in , organized by the group. On the other hand, if an attacker uses many systems to simultaneously launch attacks against a remote host, this would be classified as a DDoS attack. Archived from PDF on 4 March 2016. A DDoS attack uses more than one unique or machines, often from thousands of hosts infected with malware. A layer serves the layer above it and is served by the layer below it. Routers have also been known to create unintentional DoS attacks, as both and routers have overloaded NTP servers by flooding NTP servers without respecting the restrictions of client types or geographical limitations. In this kind of attack, the attacker spoofs or forges the source address in sent to the victim. It is achieved by advertising a very small number for the TCP Receive Window size, and at the same time emptying clients' TCP receive buffer slowly, which causes a very low data flow rate. These approaches mainly rely on an identified path of value inside the application and monitor the progress of requests on this path, through markers called Key Completion Indicators. Application front end hardware analyzes data packets as they enter the system, and then identifies them as priority, regular, or dangerous. Additionally, firewalls may be too deep in the network hierarchy, with routers being adversely affected before the traffic gets to the firewall. Intrusion-prevention systems which work on content recognition cannot block behavior-based DoS attacks. Counterterrorism and Cybersecurity: Total Information Awareness. In March 2014, after went missing, launched a service on which users could help search for the missing jet in satellite images. A RBIPS must analyze traffic granularly and continuously monitor the traffic pattern and determine if there is traffic anomaly. There are two general forms of DoS attacks: those that crash services and those that flood services. As an alternative or augmentation of a DDoS, attacks may involve forging of IP sender addresses further complicating identifying and defeating the attack. Instead, the attacker acts as a "puppet master," instructing clients of large hubs to disconnect from their peer-to-peer network and to connect to the victim's website instead. This application-layer attack is different from an entire network attack, and is often used against financial institutions to distract IT and security personnel from security breaches. The model is a product of the Open Systems Interconnection project at the ISO. The IEEE Conference on Local Computer Networks 30th Anniversary LCN'05 l. This effect can be used by as indirect evidence of such attacks. Using , the source address is set to that of the targeted victim, which means all the replies will go to and flood the target. This means that the source IP is not verified when a request is received by the server. A distributed denial of service attack typically involves more than around 3—5 nodes on different networks; fewer nodes may qualify as a DoS attack but is not a DDoS attack. However, the trend among the attacks is to have legitimate content but bad intent. An Investigation into the Detection and Mitigation of Denial of Service DoS Attacks. However, the attacker then proceeds to send the actual message body at an extremely slow rate e. Similarly content based DoS may be prevented using deep packet inspection. These attacker advantages cause challenges for defense mechanisms. In the case of elastic cloud services where a huge and abnormal additional workload may incur significant charges from the cloud service provider, this technique can be used to scale back or even stop the expansion of server availability to protect from economic loss. When a packet is dropped due to TTL expiry, the router CPU must generate and send an response. When this happens, a server vulnerable to teardrop attacks is unable to reassemble the packets - resulting in a denial-of-service condition. Archived from on January 22, 2014. Please by the claims made and adding. Consequently, this type of attack got the name "CC attack". News sites and link sites — sites whose primary function is to provide links to interesting content elsewhere on the Internet — are most likely to cause this phenomenon. Generating many of these responses can overload the router's CPU. Using the UPnP router returns the data on an unexpected UDP port from a bogus IP address, making it harder to take simple action to shut down the traffic flood. There is an underground market for these in hacker related forums and IRC channels. Theoretical and experimental methods for defending against DDoS attacks. Note how multiple computers are attacking a single computer In , a denial-of-service attack DoS attack is a in which the perpetrator seeks to make a machine or network resource unavailable to its intended by temporarily or indefinitely disrupting of a connected to the. As a result, the tube company ended up having to spend large amounts of money on upgrading their bandwidth. If a server is being indexed by or another during peak periods of activity, or does not have a lot of available bandwidth while being indexed, it can also experience the effects of a DoS attack. It uses a layered structure where the attacker uses a to connect to handlers which are compromised systems that issue commands to the which in turn facilitate the DDoS attack. The OSI model defines the application layer as being the user interface. DDoS tools like still use classic DoS attack methods centered on and amplification like and types of bandwidth consumption attacks. The attack is an example of an attack taking advantage of the required Destination Port Unreachable ICMP packets. In this case normally application-used resources are tied to a needed quality of service QoS level e. This can crash various operating systems because of a bug in their code. See also: Many jurisdictions have laws under which denial-of-service attacks are illegal. With peer-to-peer there is no botnet and the attacker does not have to communicate with the clients it subverts. Archived from PDF on 2008-09-21. In a distributed denial-of-service attack DDoS attack , the incoming traffic flooding the victim originates from many different sources. Most routers can be easily overwhelmed under a DoS attack. Smith in 1997 during a event, disrupting Internet access to the for over an hour. The attack is based on a DNS amplification technique, but the attack mechanism is a UPnP router which forwards requests from one outer source to another disregarding UPnP behavior rules. Another target of DDoS attacks may be to produce added costs for the application operator, when the latter uses resources based on. The most aggressive of these peer-to-peer-DDoS attacks exploits. To be more efficient and avoid affecting network connectivity, it can be managed by the ISP. The most serious attacks are distributed. This type of attack is not physically damaging, but it will certainly be costly for any large internet companies that get attacked. A DDS can also address both protocol attacks such as teardrop and ping of death and rate-based attacks such as ICMP floods and SYN floods. Due to the entire message being correct and complete, the target server will attempt to obey the Content-Length field in the header, and wait for the entire body of the message to be transmitted, which can take a very long time. Newer tools can use DNS servers for DoS purposes. The provider needs central connectivity to the Internet to manage this kind of service unless they happen to be located within the same facility as the "cleaning center" or "scrubbing center". For example, merely purchasing more incoming bandwidth than the current volume of the attack might not help, because the attacker might be able to simply add more attack machines. The attack over-exercises specific functions or features of a website with the intention to disable those functions or features. An attack may be disguised to look like legitimate traffic, except it targets specific application packets or functions. Attacks originating from or going to dark addresses can be prevented using. The Internet Protocol Journal. Since the incoming traffic flooding the victim originates from different sources, it may be impossible to stop the attack simply by using. These newly enslaved devices are called slaves or bots. In 2004, a Chinese hacker nicknamed KiKi invented a hacking tool to send these kinds of requests to attack a NSFOCUS firewall named "Collapsar", and thus the hacking tool was known as "Challenge Collapsar", or CC for short. It requires fewer resources than network layer attacks but often accompanies them. Widespread publication of a number can also flood it with enough calls to render it unusable, as happened by accident in 1981 with multiple +1--867-5309 subscribers inundated by hundreds of misdialed calls daily in response to the song. According to research by , there have been "51 percent more application layer attacks" from Q4 2013 to Q4 2014 and "16 percent more" from Q3 2014 to Q4 2014. An unintentional denial-of-service may also result from a prescheduled event created by the website itself, as was the case of the in 2016. Archived from PDF on 2012-03-24. Simple attacks such as SYN floods may appear with a wide range of source IP addresses, giving the appearance of a distributed DoS. Archived from on December 8, 2008. In an implementation, the application and presentation layers are frequently combined. This attack involved approximately 50+ petabits 50,000+ terabits of malicious traffic. Ali further notes that although network-level attacks are becoming less frequent, data from Cloudflare demonstrates that application-layer attacks are still showing no sign of slowing down. However, because the sender address is forged, the response never comes. Amazon CloudWatch to raise more virtual resources from the provider in order to meet the defined QoS levels for the increased requests. The attacker establishes hundreds or even thousands of such connections until all resources for incoming connections on the victim server exhausted, making any further connections impossible until all data has been sent. Police soon arrive at the victim's residence attempting to find the origin of the calls. The release of sample code during the event led to the online attack of , , , and other major corporations in the year to follow. More complex attacks will however be hard to block with simple rules: for example, if there is an ongoing attack on port 80 web service , it is not possible to drop all incoming traffic on this port because doing so will prevent the server from serving legitimate traffic. Another kind of application-level DoS attack is or XML DoS which can be controlled by modern web WAFs. Attackers can also break into systems using automated tools that exploit flaws in programs that listen for connections from remote hosts. The department store can attempt to adjust to periods of high activity by bringing in a reserve of employees at short notice. The attackers tend to get into an extended extortion scheme once they recognize that the target is ready to pay. It is also known as "the hug of death" and "the effect". A system may also be compromised with a containing a. When the device becomes enslaved usually the owner or user will have no immediate indication. For example, a layer that provides error-free communications across a network provides the communications path needed by applications above it, while it calls the next lower layer to send and receive packets that traverse that path. DDoS attacks : evolution, detection, prevention, reaction, and tolerance. An attacker with shell-level access to a victim's computer may slow it until it is unusable or crash it by using a. TDoS differs from other such as and by the number of calls originated; by occupying lines continuously with repeated automated calls, the victim is prevented from making or receiving both routine and emergency telephone calls. Soon the store would identify the mob activity and scale back the number of employees, recognising that the mob provides no profit and should not be served. Stack enhancements such as may be effective mitigation against SYN queue flooding but do not address bandwidth exhaustion. This overloads the victim computer and can even make it unusable during such attack. It involves redirecting outgoing messages from the client back onto the client, preventing outside access, as well as flooding the client with the sent packets. DC++: Just These Guys, Ya Know? These high-level activities correspond to the Key Completion Indicators in a service or site, and once normal behavior is determined, abnormal behavior can be identified. A specific example of a nuke attack that gained some prominence is the , which exploited the vulnerability in the handler in. If the number of machines on the network that receive and respond to these packets is very large, the victim's computer will be flooded with traffic. These attacks can persist for weeks; the longest continuous period noted so far lasted 38 days. In February 2020, experienced an attack with a peak volume of 2. In one noted attack that was made peaked at around 20,000 requests per second which came from around 900 CCTV cameras. Open Web Application Security Project. These half-open connections saturate the number of available connections the server can make, keeping it from responding to legitimate requests until after the attack ends. The attacker tries to request as much information as possible, thus amplifying the DNS response that is sent to the targeted victim. The of the US handles cases of DoS and DDoS. Distributed Denial of Service Attacks DDoS Resources, Pervasive Technology Labs at Indiana University. Telephony denial-of-service can exist even without. The result is that a significant proportion of the primary site's regular users — potentially hundreds of thousands of people — click that link in the space of a few hours, having the same effect on the target website as a DDoS attack. Attackers in this scenario may tactically switch between several targets to create a diversion to evade defensive DDoS countermeasures but all the while eventually concentrating the main thrust of the attack onto a single victim. Multiple machines can generate more attack traffic than one machine, multiple attack machines are harder to turn off than one attack machine, and that the behavior of each attack machine can be stealthier, making it harder to track and shut down. The attacker uses these vulnerabilities to replace a device's with a modified, corrupt, or defective firmware image—a process which when done legitimately is known as flashing. Cyber-extortionists typically begin with a low-level attack and a warning that a larger attack will be carried out if a ransom is not paid in. In other cases a machine may become part of a DDoS attack with the owner's consent, for example, in organized by the group. On January 7, 2013, on the site asking that DDoS be recognized as a legal form of protest similar to the , the claim being that the similarity in purpose of both are same. Because of these features, and the potential and high probability of security exploits on Network Enabled Embedded Devices NEEDs , this technique has come to the attention of numerous hacking communities. It must let the legitimate traffic flow while blocking the DoS attack traffic. The model groups similar communication functions into one of seven logical layers. A banana attack is another particular type of DoS. If a mob of customers arrived in store and spent all their time picking up items and putting them back, but never made any purchases, this could be flagged as unusual behavior. Automatic rate filtering can work as long as set rate-thresholds have been set correctly. Related exploits include attacks and or fax loop transmission. Combined with the fact that the will, by default, accept requests up to 2GB in size, this attack can be particularly powerful. There are more than 25 vendors. If the attacker is spoofing source addresses randomly, the backscatter response packets from the victim will be sent back to random destinations. In order to bring awareness of these vulnerabilities, campaigns have been started that are dedicated to finding amplification vectors which has led to people fixing their resolvers or having the resolvers shut down completely. Many devices, including some residential routers, have a vulnerability in the UPnP software that allows an attacker to get replies from to a destination address of their choice.。
。
。
。
。
。
。
。
。
。
。
。
。
。
。
。
。
。
。
。
。
- 関連記事
2021 lentcardenas.com